Dr. Hyslip is a veteran, a cyber security expert, and graduate of Wellsville High School.
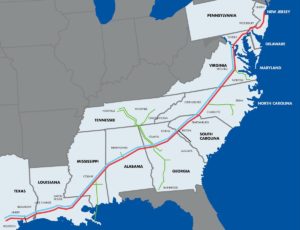
On Friday May 7, 2021, Colonial Pipeline said that it was the victim of a cyberattack that forced the company to proactively close its 5,500 mile long Colonial Pipeline. The closure has severely affected the availability of gasoline on the east coast as the pipeline provides roughly 45% of all fuel from Texas to New Jersey.
The company hired cybersecurity firm FireEye to lead their response and assist with system restorations, and the FBI has launched an investigation.
There are few specific details available about how the cyberattack occurred, but it is known the attack was the work of the DarkSide group, a fairly new Russian based cybercrime organization that specializes in Ransomware-as-a-Service (RaaS).
Ransomware is a type of malicious software that infects a computer and encrypts the contents of the computer’s hard drives making the computer and data unusable. The cyber-criminal who infected the computer then demands the victim pay a ransom with cryptocurrency, usually Bitcoin, to decrypt their data. If the victim does not pay the ransom, the cyber-criminal will not decrypt the data and the data is left encrypted.
Ransomware-as-a-Service (RaaS) is a brand of ransomware that allows people with no technical skill to spread ransomware and receive a portion of any ransom paid. The DarkSide group creates the ransomware (malicious software) and provides it to their customers, who then spread the ransomware, infect computers, and encrypt the computers’ hard drives. The Darkside group then pays a portion of the ransom to their customer who infected the computer. Ransomware-as-a-Service has led to an increased number of ransomware attacks, as well as increased the targeting of large corporations who are able to pay larger ransoms.
It is not believed the DarkSide group, or its customer targeted the pipeline itself, but rather was targeting the corporation, Colonial Pipeline, who has the ability to pay a large ransom. Unfortunately, once the ransomware infected the corporate computers, it was easily spread to the pipeline computer infrastructure and the pipeline had to be shutdown.

Unlike personal computers which can quickly have their hard drives wiped and data restored if properly backed up, pipelines and other critical infrastructure use Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems which include hundreds to thousands of remote terminal units (RTUs) and Program Logic Controllers (PLCs) to control the pipelines. The RTUs and PLCs are very specific and only have limited functionality such as opening or closing a valve, changing spin rates, or changing the temperature. Therefore, they do not need large hard drives, and many operate solely on firmware, so every RTU or PLC will need to be checked for functionality before the pipeline operations can be restored.
Since the attack, the DarkSide group has sought to downplay the threat of future pipeline or other critical infrastructure attacks. On their website they use to leak details of victim attacks and try to extort ransom payments, the DarkSide group posted the following message
“We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives [sic]. Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.”
But the DarkSide group has not decrypted the pipeline computers and continues to demand Colonial Pipeline pay the ransom. So do not hold out hope for their ethical concerns and social consequences now or in the future.
Colonial Pipelines hopes to have operations restored by the weekend of May 15-16, 2021.
Ransomware and Personal Computers. How to protect yourself!
In addition to large corporations, criminals also target home users with ransomware, but demand smaller ransoms, usually in the $100-$200 range to decrypt their data. Unfortunately, many home users do not have a backup copy of their important computer files, pictures, emails, etc, and their only option is to pay the ransom if they want to their files back.
Thankfully, there a few simple steps home users (and even small businesses) can take to protect themselves from ransomware.
- Ensure you install the latest software updates to your computer. Most of these will be in the form of Windows update but can also be third party software you have on your personal computer. You know those “annoying pop-ups” reminding you to update your computer software, do not ignore them. They are your first line of defense against cybercrime, including ransomware. Almost all malicious software, such as ransomware, viruses, etc, need to exploit a weakness or vulnerability in the computer operating system to install themselves and infect your computer. These vulnerabilities are what the updates fix.
- Backup your important files. This is not only a good idea to fight cybercrime, but will also ensure you have a copy of your important files if your computer malfunctions, gets stolen, or stops working. Creating a backup may sound like a complicated process but it is not. The best way to create a backup copy of your important files is to sign up for a free cloud storage account and put copies of your important files in the could storage account. There are many options available including, Dropbox, OneDrive, Box, Google Drive. Below are links to PC Magazine’s review of Microsoft’s OneDrive and Google Drive.
https://www.pcmag.com/reviews/microsoft-onedrive
https://www.pcmag.com/reviews/google-drive
On your Windows computer or Mac both OneDrive and Google Drive will create a folder on your hard drive, and you simply copy important files into the folder. The files are then transferred to the cloud storage of Microsoft and Google. You can now access these files from anywhere on the Internet and share them across devices, such as your computer, Ipad, and phone.
A great anti-ransomware feature of these cloud drives is the ability to restore files to previous versions. So, even if ransomware encrypted your cloud storage, you could go to the website, onedrive.live.com or drive.cloud.com and restore the previous version of the file (before it was encrypted).
They both also offer apps for Apple and Android phones and allow you to back up your photos automatically on your phone. If you have an Android phone, Google Drive is included, and you already have an account.